AWS web interface
AWS web interface serves over a million active guests in further than 240 countries and homes. As our guests grow their businesses, AWS...
IBM Recruitment Drive 2021
IBM Recruitment Drive 2021
IBM India Pvt. Limited is hiring for the position of Data Scientist.
Job Description:
As a Data Scientist at IBM, you will help...
Society’s Challenges
What are the newly existing challenges in the society?
Society-education-problems-challenges. Society's Challenges-(Meaning):-In today's world, our country is developing at all levels. with this development, new...
Troubleshooting
Troubleshooting is a form of problem solving, often applied to repair failed products or processes on a machine or a system. It is a logical,...
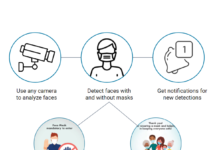
Face Mask Detection
Face Mask Detection is a technology capable of matching a human face from a digital image or a video frame against a database of faces, typically employ to authenticate users through ID verification services, works...
Social media
Social media is a computer-based technology that facilitates the sharing of ideas, thoughts. And information through the building of virtual networks and communities. By design, this...
Social engineering
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. This differs from social engineering within the social sciences,...
Child Labour
Child Labour refers to the exploitation of children through any form of work that deprives children of their childhood, interferes with their ability to attend...
Basic Characteristics of India as a Developing Economy
India, as a developing country, features a mixed economy in the world.
The major characteristics of developing economy are low per capita income, overpopulation, maximum population...
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent ("spoofed") message designed to trick a human victim into revealing sensitive information to the attacker or...