Cyber threat hunting is a proactive security search through networks, endpoints, and datasets to hunt malicious, suspicious, or risky activities that have evaded detection by existing tools. Thus, there is a distinction between cyber threat detection versus cyber threat hunting. Threat detection is a somewhat passive approach to monitoring data and systems for potential security issues, but it’s still a necessity and can aid a threat hunter. Proactive cyber threat hunting tactics have evolved to use new threat intelligence on previously collected data to identify and categorize potential threats in advance of attack.
Security personnel can’t afford to believe that their security system is impenetrable. They must remain ever vigilant for the next threat or vulnerability. Rather than sit back and wait for threats to strike, cyber threat hunting develops hypotheses based on knowing the behaviors of threat actors and validating those hypotheses through active searches in the environment. With threat hunting, an expert doesn’t start from an alert or even Indicators of Compromise (IOC) but deeper reasoning and forensics. In many cases the hunter’s efforts create and substantiate the alert or IOC. Cyber threat hunting aggressively assumes that a breach in the enterprise has or will occur. Security personnel hunt down threats in their environment rather than deploy the latest tool.
Five threat hunting steps
Step 1: Hypothesis
Threat hunts begins with a idea of what threats might be there and how to find them. A hypothesis can include a suspected attacker’s tactics, techniques, and procedures (TTPs). Threat hunters use threat intelligence, environmental knowledge, and their own experience and creativity to build a logical path to detection.
Step 2: Collect and Process Intelligence and Data
Hunting for threats requires quality intelligence and data. Security Information and Event Management (SIEM)can provide insight and a track record of activities.
Step 3: Trigger
A hypothesis can act as a trigger when advanced detection tools point threat hunters to initiate an investigation of a particular system or specific area of a network.
Step 4: Investigation
Investigative technology, such as Endpoint Detection and Response (EDR), can hunt or search deep into potentially malicious anomalies in a system or network, ultimately determined to be benign or confirmed as malicious.
Step 5: Response/Resolution
Data gathered from confirmed malicious activity can be entered into automated security technology to respond, resolve, and mitigate threats. Actions can include removing malware files, restoring altered or deleted files to their original state, updating firewall /IPS rules, deploying security patches, and changing system configurations – all the while better understanding what occurred and how to improve your security against similar future attacks.
Benefits of threat hunting
- Speed and accuracy of response
- Attack surface exposure / hardened network and endpoints
- Reducing dwell time (infection to detection)
- Time to containment (detect/prevent the spread or lateral movement)
- Amount of actual breaches based on the number of incidents detected
- Exposure to external threats
- Resources spent on response
- Reducing frequency/Number of malware infections
What’s required for cyber threat hunting?
What basic security resources does an enterprise need to activate threat hunting or in a threat hunting service?
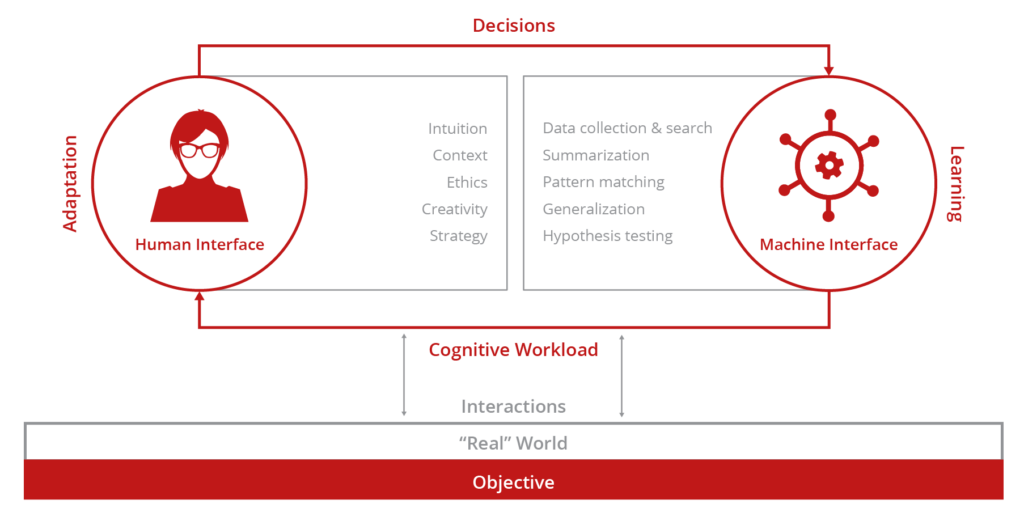
Optimize Human Expertise Through Human Machine Teaming.