A SOC analyst is a cybersecurity professional who works as part of a team to monitor and fight threats to an organization’s IT infrastructure, and to assess security systems and measures for weaknesses and possible improvements. The SOC in the job title stands for security operations center; this is the name for the team, which consists of multiple analysts and other security pros, and often works together in a single physical location. A SOC may be an internal team serving a single enterprise or an outsourced service providing security for one or more external clients.
SOC Analyst Requirements
To become a successful SOC Analyst, it is important that you meet the necessary criteria that are generally demanded by most organizations around the world. Here, you will read about the education qualification you need, along with the skill set you must master, to get into this job profile.
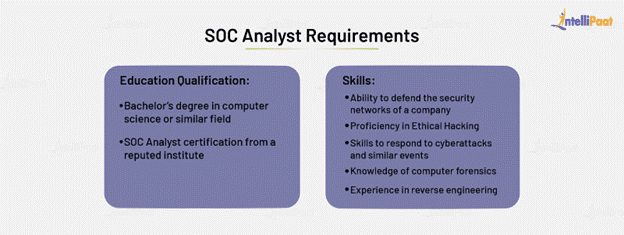
Education Qualification to Be a SOC Analyst
To start with you need a Bachelor’s degree in CS field or any other similar sectors.
Further you can also obtain a certification of Certified SOC Analyst (CSA) through a well-reputed institute.
Skills:-
The CSA program can help a SOC analyst acquire the necessary skills to become a Tier I and subsequently a Tier II analyst.
Here’s how the two differ:
Tier I SOC analyst
Often considered as a triage specialist with system administration skills in Linux, Windows, and macOS. A Tier I SOC analyst is also well-versed in Ruby on Rails, Python, PHP, C, C#, Java, and Perl. He or she helps team members review all incident alerts and determine their urgency. It also elevates priority concerns to their Tier II counterparts.
Tier II SOC analyst
Also called an “incident responder.” A Tier II SOC analyst reviews tickets sent by his or her Tier I counterparts. He or she gathers new threat intelligence to determine the scope of an attempt or ongoing attack.
Tools Do SOC Analysts Often Use?
Since SOC analysts need to develop holistic security protection protocols, they need to use all available resources. Some of the open-source tools they can use are:
- Delta: It helps detect potential problems within a software-defined network (SDN) and how these can be exploited. The tool can probe not only known but also unknown network vulnerabilities.
- Ettercap: This is useful for testing man-in-the-middle (MitM) attacks. It explores how an environment responds to such an attack.
- HoneyNet: This helps analysts study commonly used attack patterns to come up with strategies to deceive perpetrators helping safeguard network.
- Infection Monkey: This is a tool that reveals events that can occur within a network once an attacker gains access.
- Lynis: This reveals all utilities and applications in Unix-based systems, including their configurations and vulnerabilities.
- Maltego: Primarily used for data mining and link analyses, Maltego provides a library of transformations for investigating threats.
- Nagios: This helps monitor an entire network, including infrastructure, traffic, and all connected servers.
- OpenVAS: This is a scanner that assesses and identifies assets that have vulnerabilities that can leave a network open to a security attack.
- Swiggy Off Campus Drive 2024 For Freshers – Must Apply Instantly
- Ericsson Careers Recruitment 2024 | Apply before last date
- Yash Technologies Recruitment Drive 2024 – Must Apply Instantly
- BCG Internship Drive For Freshers 2024 – Must Apply Instantly
- Harman Careers Recruitment 2024 | Freshers must apply