Intrusion Detection System (IDS)
Intrusion Detection is an important technology that monitors network traffic and Events. Intrusion Detection System also identifies network intrusions such as abnormal network behaviors,...
Data Compression In The Technology
Compression : Data Compression In The Technology
Data Compression In The Technology : File compression is the practice of packaging a file. Files to...
Multimedia communication
Multimedia communication deals with the transfer, protocols, services, and mechanisms of discrete media data and continuous media data over digital networks.
It can be recorded for...
Software configuration management and its objectives
Software Configuration Management (SCM) can be define as a process of defining and implementing a standard configuration. which results in easier setup and maintenance...
STL : How can we use it and why it is important ?
This one of the most using and adapting skills for coding. STL allows us to have many styles in programming context. As a result,...
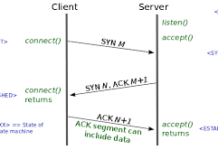
HTTP protocol , its characteristics and evolutions.
Generally protocol refers to a set of rules and regulations to perform certain task. As we know, we create websites using HTML which is...
Coding languages that one should prefer to use
It has become a vital role and to know coding. As a result, coding is way where human is trying to explain and out...
Cogito ‘s Intelligence Augmentation (IA) for AI
ABOUT COMPANY
AI coaching that goes beyond traditional speech analytics. Cogito is the market leader in human-centred AI coaching, with over a decade of advanced R&D...
HomeLane: Backend Hiring Challenge
ABOUT COMPANY
About HomeLane:
Started in 2014, Homelane is a technology-driven solution provider for personalized home interiors. We focus on the predictability and quality of the...
Zynga Diversity Game Development Hiring Challenge
ABOUT COMPANY
Zynga was founded in 2007 with the vision that play would become one of the core activities on the Internet. We pioneered social...