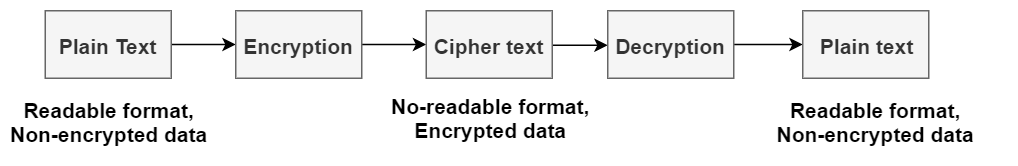
What is Cryptography?
Cryptography provides for secure communication in the presence of malicious third-parties—known as adversaries.
This form of process intercepts unauthorized accessibility for the data. Encoding of information in cryptography follows mathematical hypotheses and few calculations described as algorithms.
Cryptography Types
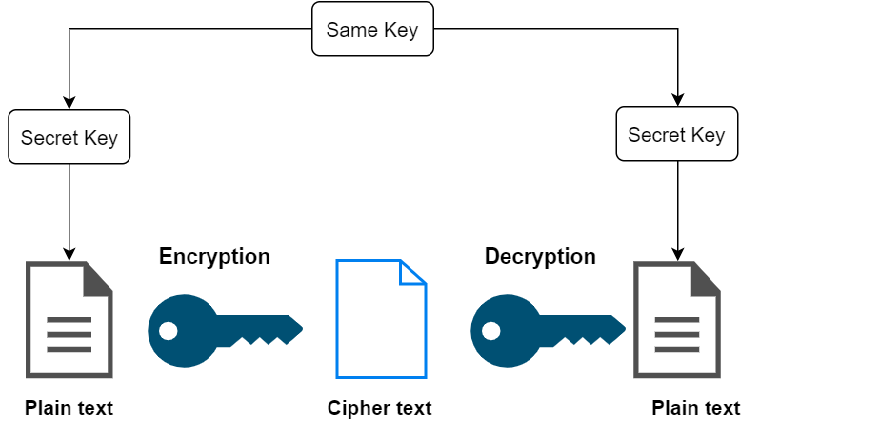
Few types of Symmetric key cryptography are
- Block
- Block cipher
- DES (Data Encryption System)
- RC2
- IDEA
- Blowfish
- Stream cipher
Asymmetric Key Cryptography
It follows a varied and protected method in the transmission of information. The frequent kind of cryptography used in this method is RSA. Few of the kinds of Asymmetric key cryptography are:
- RSA
- DSA
- PKCs
- Elliptic curve techniques
- asymmetric encryption
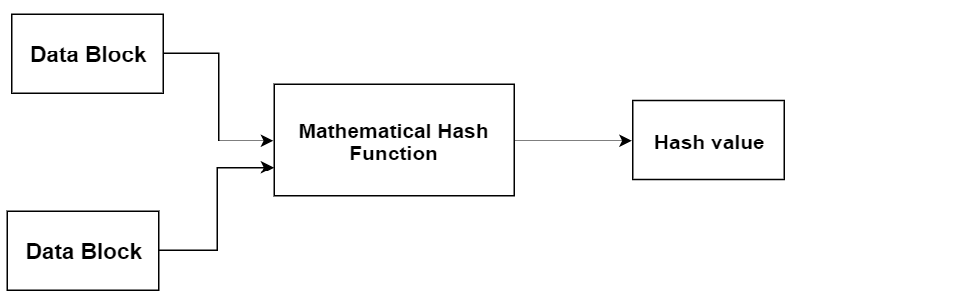
Hash Function
This method will not need any kind of key as it functions in a one-way scenario. Few of the functionalities of the hash are:
- Message Digest 5 (MD5)
- RIPEMD
- Whirlpool
- SHA (Secure hash Algorithm)
Cryptography Tools
Cryptography tools are more useful in the situations of signature confirmation, code signing and to perform other cryptography activities.
SignTool.exe
With the timestamp in the file, it holds the ability to authenticate the file. The whole feature in SignTool.exe ensures for augmented reliability of the file shared server.
Authentication Using Key
Here, the encrypted information has to be decrypted through keys. This tool has two kinds of encryption techniques and those are:
- Symmetric Key Cryptography
- Asymmetric Key Cryptography
Blowfish
This encryption algorithm split up messages into clocks having 64 bits and encrypts these clocks separately. The captivating feature that lies in Blowfish is its speed and efficacy. As this is an open algorithm for everyone, many gained the benefits of implementing this. All these allow this algorithm to be most prominent in the market.
Applications of Cryptography
Applications for cryptography as below.
Conventionally, cryptography was in implementation only for securing purposes of security methods.





